Welcome to the intriguing world of digital security, where the significance of Passkey plays a crucial role in safeguarding sensitive information. In this article, we will delve into the history, benefits, advantages, and drawbacks of Passkey, shedding light on its evolution in enhancing user authentication and data protection. Stay tuned to uncover the pivotal role that Passkey plays in ensuring robust security measures in today’s interconnected digital landscape.

Definition of Passkey
In the realm of digital security, a passkey serves as a fundamental shield, safeguarding sensitive realms of data and systems. By definition, a passkey is the cryptographic linchpin, a code or password, acting as an impenetrable gatekeeper granting access solely to authorized users. This pivotal tool holds the power to fortify user authentication processes, erecting barriers to thwart unauthorized incursions into vital digital domains.
Such a passkey, though seemingly simple in form, carries profound implications in the intricate tapestry of digital security. It stands as a sentinel, vigilantly monitoring the gates of digital fortresses, ensuring that only those possessing the rightful key can traverse the labyrinth of information. Without this crucial authentication mechanism, the integrity and confidentiality of data and systems would be perilously compromised, exposing them to a myriad of potential threats and breaches.
Hence, the significance of the humble passkey resonates deeply within the digital landscape, embodying the essence of trust and security. It is the bedrock upon which the pillars of data sanctity and system integrity firmly rest, symbolizing the essence of protection in a realm fraught with digital perils. With its omnipresent importance in maintaining the sanctity of digital realms, the passkey emerges as the stalwart guardian, upholding the sanctity and inviolability of information and systems in a cyber-centric world.

History of Passkey
Passkey: A Revolutionary Evolution
Passkey, an alternative authentication method, has been a beacon of security since early computer days, challenging conventional password systems. Its inception marked a shift towards enhanced protection, with the evolution embracing 2FA and MFA technologies for robust defense mechanisms.
From Simple Code to Sophisticated Defense
The journey of Passkey is a testament to the relentless pursuit of digital security. What began as a mere code has transcended into sophisticated layers of protection, integrating technologies like 2FA and MFA to fortify digital barriers against evolving cyber threats.

Advantages of Passkey
In the realm of digital security, the significance of Passkey emerges through its seamless usability. Unlike physical keys or tokens, Passkeys offer a user-friendly approach, simplifying access management processes for administrators and end-users alike. This ease of use fosters a smoother and more efficient authentication experience, enhancing overall system usability and convenience.
When delving into the core essence of Passkey, one cannot overlook its robust security features. The complexity and intricate nature of Passkeys contribute to creating a formidable defense against unauthorized access attempts. By incorporating a Passkey that is hard to decipher or guess, organizations can elevate their security posture, safeguarding sensitive information and assets from potential threats in the digital landscape.
Furthermore, the dynamic nature of Passkeys empowers administrators with a powerful tool for user access management. By offering the flexibility to change Passkeys as needed, system administrators can efficiently adapt to evolving security requirements and user permissions. This agility not only enhances security protocols but also streamlines the process of granting or revoking access, ensuring a proactive and responsive approach to safeguarding digital assets.

Drawbacks of Passkey
When considering the significance of Passkey in digital security, it’s crucial to acknowledge its drawbacks. One significant risk is the potential for users to forget their codes or passwords, resulting in restricted access or data loss. This issue underscores the importance of implementing robust backup and recovery mechanisms to mitigate such risks effectively.
Another notable drawback of Passkeys is their vulnerability to brute force attacks, where malicious actors attempt multiple combinations to crack the Passkey. This exposes systems to security breaches and unauthorized access if stringent security measures, such as encryption and multifactor authentication, are not in place to counter such threats effectively.
Moreover, Passkeys are susceptible to exploitation through phishing and social engineering tactics, posing a serious threat to digital security. Attackers may deceive users into revealing their Passkeys through fraudulent emails or messages, compromising sensitive information and jeopardizing the integrity of digital systems. Vigilance and user education are vital in combating such threats effectively.
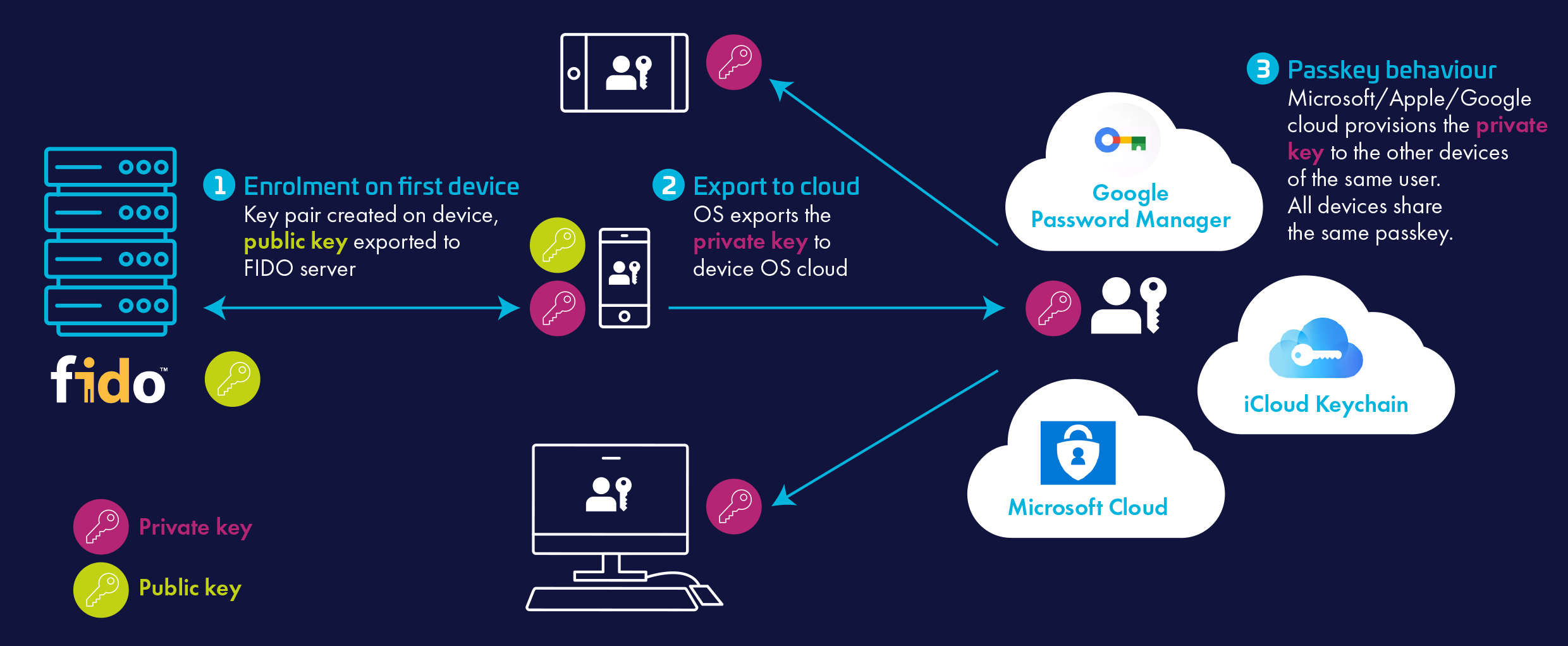
Conclusion
In the intricate landscape of digital security, the significance of passkeys stands out as a critical asset. Acting as a formidable shield, passkeys fortify the walls safeguarding sensitive data and systems, acting as a first line of defense against cyber threats. Their role extends beyond mere protection, delving into the realm of user convenience and authentication, elevating user experiences to new heights with enhanced security protocols.
Passkeys, revered for their ability to add an extra layer of security, play a pivotal role in the intricate dance of digital protection. By requiring this unique code, the digital realm becomes fortified, ensuring that only authorized users gain access to crucial information. This meticulous process not only keeps data safe but also instills confidence in users, fostering a sense of security that transcends mere passwords.
Embracing passkeys signifies a commitment to robust, impenetrable security measures in the ever-evolving digital sphere. Their prowess in strengthening authentication mechanisms elevates user trust and satisfaction, making interactions smoother and safer. As technology advances and cyber threats loom larger, the significance of passkeys as gatekeepers of digital fortresses becomes more pronounced, underlining their indispensable nature in ensuring the integrity of digital ecosystems.
